Three pictures tell you the principles of Linux TCP/IP protocol stack
|
It is no exaggeration to say that today's Internet is built on TCP/IP. Understanding the principles of the protocol stack is very helpful for debugging network IO performance and solving network problems. This article will take you to see how the kernel controls network data flow. TCP Features We all know that the original intention of TCP protocol design is to ensure fast, orderly and error-free data transmission. So the characteristics are summarized as follows:
After understanding the characteristics of TCP, let's take a look at the actual process of data transmission.
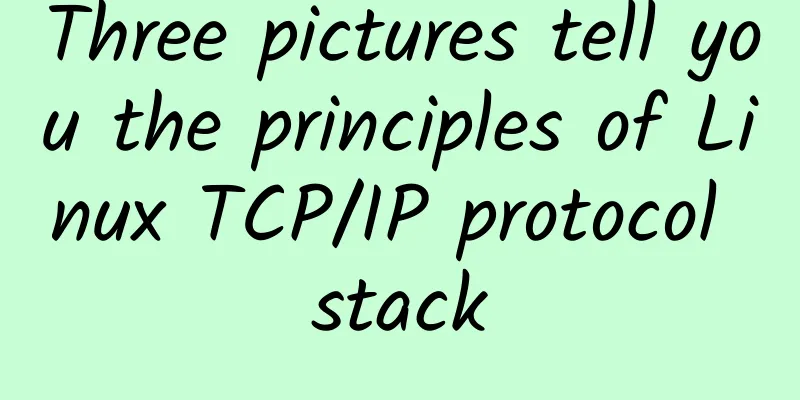
Data transmission Let’s first look at the picture: The figure above shows the process of data flow in hardware, and the figure below shows the process of data in the protocol stack: The whole process is divided into three major areas: user area, kernel area, and device. The device here is the network card. The process is as follows:
Data Reception Look directly at the hardware data flow diagram: First, the NIC writes the received data packet into its memory. Then it verifies it and sends it to the host's main memory. The buffer in the main memory is allocated by the driver, and the driver will tell the NIC the allocated buffer description. If there is not enough buffer to receive the NIC's data packet, the NIC will discard the data packet. Once the data packet is copied to the main memory, the NIC will inform the host OS through an interrupt. The driver then checks if it can handle the new packet. If it can, the driver will package the data packet into a structure that the OS recognizes (linux sk_buffer) and push it to the upper layer. After the link layer receives the frame and checks if it passes, it will deframe it according to the protocol and push it to the IP layer. After unpacking, the IP layer will decide whether to push the packet to the upper layer or forward it to other IPs based on the IP information contained in the packet. If it is determined that it needs to be pushed to the upper layer, the IP header will be unpacked and pushed to the TCP layer. After decoding the message, TCP will find the corresponding TCB according to its four-tuple, and then process the message through the TCP protocol. After receiving the message, it will add the message to the receiving message, and then send an ACK to the other end according to the TCP status. Of course, the above process will be affected by NAT and other Netfilters, which we will not discuss here and have not studied in depth. Of course, for the sake of performance, experts have also made a lot of efforts in various aspects, such as RDMA, DPDK and other major software and hardware technologies, and zero-copy, checksum offload, etc.; Summarize Modern hardware and software TCP/IP protocol stacks have no problem sending 1~2GiB/s over a single link (tested). If you want to explore better performance, you can try technologies such as RMDA, which optimize performance by bypassing the kernel to reduce copying, etc., but this may depend on the hardware. |
>>: How is IPv6 represented? How is IPv4 converted to IPv6?
Recommend
What is missing from the 5G development of radio and television? The fourth largest operator faces four challenges
At the beginning of 2020, there are constant news...
How to unleash greater potential of new infrastructure
Recently, several domestic mobile communication o...
Authoritative interpretation from the Ministry of Industry and Information Technology: What exactly is "5G+Industrial Internet"?
[[415906]] Recently, the Information and Communic...
iWebFusion dedicated server starts from $49/month, 4-40 core CPU, 384G memory, NVMe hard disk, 1-10G bandwidth, multiple computer rooms in Los Angeles and other places
iWebFusion (formerly iWFHosting) is a hosting com...
What does a Web Application Firewall do? How is it different from traditional network devices?
What is a WAF? The full name of WAF is (Web Appli...
What role does a switch play in a network?
Switches play an important role in increasing the...
During the COVID-19 pandemic, F5 ensures safe and stable remote work for Lancashire hospitals in the UK
Lancashire Teaching Hospitals NHS Foundation Trus...
Facing Huawei 5G, the United States is showing its hand
Originally, in the context of the "big cake&...
Huawei was named "Most Innovative Company" by Brand Eins and "Best Employer" by LinkedIn in Germany.
[Düsseldorf, Germany, March 22, 2018] Huawei was ...
In the ranking of domestic mobile data usage, Tibet ranks first and Shanghai ranks second to last
Recently, the Ministry of Industry and Informatio...
This picture explains the principle of 5G
5G is getting closer and closer to us. On the 18t...
Autonomous security + high-quality experience, Ubuntu Kylin's press conference will solve your operating system problems!
In recent years, the international situation has ...
GreenCloudVPS 9th anniversary, $15/year KVM-2GB/20GB/2TB/San Jose and other data centers available
GreenCloudVPS recently launched its 9th anniversa...
What power will the combination of 5G and intelligent automation bring?
It can be said that 5G and intelligent automation...









