Linux TCP/IP protocol stack, data sending and receiving process, TCP protocol characteristics
|
It is no exaggeration to say that today's Internet is built on TCP/IP. Understanding the principles of the protocol stack is very helpful for debugging network IO performance and solving network problems. This article will take you to see how the kernel controls network data flow.
TCP Features We all know that the original intention of TCP protocol design is to ensure fast, orderly and error-free data transmission. So the characteristics are summarized as follows:
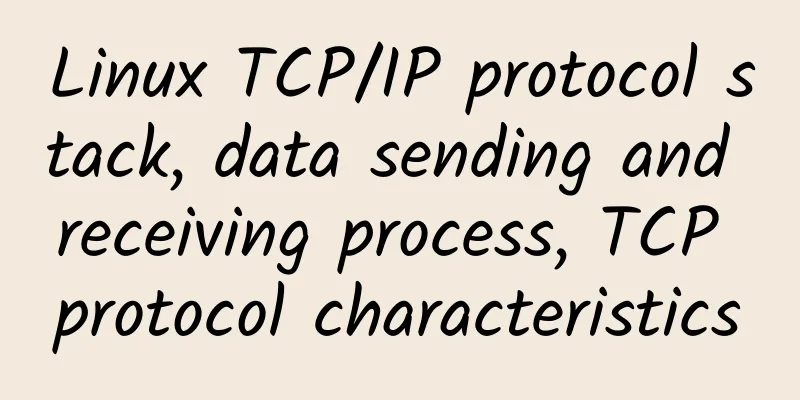
After understanding the characteristics of TCP, let's take a look at the actual process of data transmission. Data transmission Let’s first look at the picture: The figure above shows the process of data flow in hardware, and the figure below shows the process of data in the protocol stack: The whole process is divided into three major areas: user area, kernel area, and device. The device here is the network card. The process is as follows:
Data Reception Look directly at the hardware data flow diagram: First, the NIC writes the received data packet into its memory. Then it verifies it and sends it to the host's main memory. The buffer in the main memory is allocated by the driver, and the driver will tell the NIC the allocated buffer description. If there is not enough buffer to receive the NIC's data packet, the NIC will discard the data packet. Once the data packet is copied to the main memory, the NIC will inform the host OS through an interrupt. The driver then checks if it can handle the new packet. If it can, the driver will package the data packet into a structure that the OS recognizes (linux sk_buffer) and push it to the upper layer. After the link layer receives the frame and checks if it passes, it will deframe it according to the protocol and push it to the IP layer. After unpacking, the IP layer will decide whether to push the packet to the upper layer or forward it to other IPs based on the IP information contained in the packet. If it is determined that it needs to be pushed to the upper layer, the IP header will be unpacked and pushed to the TCP layer. After decoding the message, TCP will find the corresponding TCB according to its four-tuple, and then process the message through the TCP protocol. After receiving the message, it will add the message to the receiving message, and then send an ACK to the other end according to the TCP status. Of course, the above process will be affected by NAT and other Netfilters, which we will not discuss here and have not studied in depth. Of course, for the sake of performance, experts have also made a lot of efforts in various aspects, such as RDMA, DPDK and other major software and hardware technologies, and zero-copy, checksum offload, etc.; Summarize Modern hardware and software TCP/IP protocol stacks have no problem sending 1~2GiB/s over a single link (tested). If you want to explore better performance, you can try technologies such as RMDA, which optimize performance by bypassing the kernel to reduce copying, etc., but this may depend on the hardware. |
<<: 5G, edge computing and IoT are expected to reshape networks
>>: OSI seven-layer and TCP five-layer protocols, why TCP/IP protocol wins
Recommend
spinservers: $99/month - 2*E5-2630Lv3/256GB/2*1.6T SSD/10Gbps bandwidth/San Jose data center
This month, spinservers is offering a flash sale ...
Google and Qualcomm join forces to fight against Apple. Will the global 5G competition landscape be further changed?
(Original title: Google and Qualcomm join forces ...
Zigbee vs. Wi-Fi: Which is Better for Your Smart Home?
All smart home appliances rely on connectivity to...
Three-minute review! A quick overview of 5G industry development trends in December 2021
After the rapid development in 2020, 2021 is a cr...
CMIVPS: 350 yuan/year-1GB/20GB NVMe/1.5TB@1Gbps/Seattle/High Defense VPS
Many friends have given good feedback on SpartanH...
HostKvm 20% off, Singapore VPS monthly payment starts from $5.6, 2G memory/40G hard disk/50M bandwidth
HostKvm has launched a regular promotion this mon...
Lightwave OFC 2025 Outlook: Quantum will take center stage
Beijing time, February 19 (Shui Yi) As the world&...
ENOs and Private LTE: Intelligent Connectivity for Smart Factories
Manufacturing processes and operations are underg...
Samsung bets on European 5G orders to grow network equipment business
Samsung Electronics is pinning its hopes on Europ...
How to switch IT service providers with minimal business disruption
At the beginning of 2020, many organizations list...
Morphling: How to maximize cost reduction when deploying AI in cloud native?
With the vigorous development of cloud-native tec...
The Ministry of Industry and Information Technology has implemented new measures to promote the accelerated development of 5G and accelerate the construction of the new economic form of "5G+".
my country's 5G development has once again re...
my country has built the world's largest 4G network
On January 6, the Ministry of Science and Technol...
DPtech assists the Road Network Center of the Ministry of Transport to provide security support for the comprehensive establishment of a ministerial-level monitoring system for highway video networking
Recently, Deepin Technology won the bid for the h...
The outbreak of 5G still cannot prevent the overall decline of the mobile phone market
In this year hit by the epidemic, sales in the mo...









