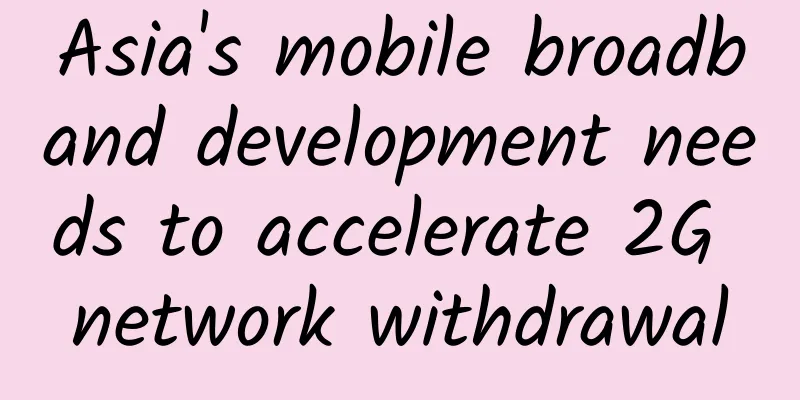
[[401440]] Network protocol stack in uboot The network card driver has already encapsulated the interface for sending and receiving data for the upper-layer protocol. Therefore, the upper-layer protocol stack only needs to call the corresponding network card driver functions in sequence to send and receive network data. The protocol stack in uboot is relatively simple and has the following characteristics: The transport layer only supports the UDP protocol; - Currently only several protocols are supported, including ICMP, TFTP, NFS, DNS, DHCP, CDP, and SNTP;
- The network card uses poll to receive data packets instead of interrupt mode;
- The sending and receiving of data packets are serial operations and do not support concurrency.
1. Network protocol stack architecture The following is the function calling process of the uboot network protocol stack: 2. Use DNS commands to analyze the sending and receiving process of a data packet In uboot, all commands are defined by the macro U_BOOT_CMD. The definition of the dns command is as follows: - 426 U_BOOT_CMD(
- 427 dns, 3, 1, do_dns,
- 428 "lookup the IP of a hostname" ,
- 429 "hostname [envvar]"
- 430 );
When we enter the command dns in the uboot command terminal, the command parsing function will call the dns execution function do_dns() - 389 int do_dns(cmd_tbl_t *cmdtp, int flag, int argc, char * const argv[])
- 390 {
- …
- 406 if (strlen(argv[1]) >= 255) {
- 407 printf( "dns error: hostname too long\n" );
- 408 return 1;
- 409 }
- 410
- 411 NetDNSResolve = argv[1];
- 412
- 413 if (argc == 3)
- 414 NetDNSenvvar = argv[2];
- 415 else
- 416 NetDNSenvvar = NULL ;
- 417
- 418 if (NetLoop(DNS) < 0) {
- 419 printf( "dns lookup of %s failed, check setup\n" , argv[1]);
- 420 return 1;
- 421 }
- 422
- 423 return 0;
- 424 }
Line 406 determines the length of the parameter string. If it is greater than 255, it is illegal. Line 411 parameter 1 must be the host to be resolved, which is stored in NetDNSResolve. Lines 413 to 416 store the environment parameters of the dns command. This parameter can be missing. Line 418 enters the network protocol processing function entry NetLoop() and passes the corresponding protocol DNS to the function. The NetLoop() code is quite long, so we will only analyze a few important sections of it. - 316 /************************************************************************/
- 317 /*
- 318 * Main network processing loop.
- 319 */
- 320
- 321 int NetLoop(enum proto_t protocol)
- 322 {
- 323 bd_t *bd = gd->bd;
- 324 int ret = -1;
- …………
- 352 NetInitLoop();
- …………
- 367 switch (protocol) {
- 368 case TFTPGET:
- 369 #ifdef CONFIG_CMD_TFTPPUT
- 370 case TFTPPUT:
- 371 #endif
- 372 /* always use ARP to get server ethernet address */
- 373 TftpStart(protocol);
- 374 break;
- …………
- 426 #if defined(CONFIG_CMD_DNS)
- 427 case DNS:
- 428 DnsStart();
- 429 break;
- 430 #endif
- 438 }
- …………
- 461 for (;;) {
- 462 WATCHDOG_RESET();
- 463 #ifdef CONFIG_SHOW_ACTIVITY
- 464 show_activity(1);
- 465 #endif
- 466 /*
- 467 * Check the ethernet for a new packet. The ethernet
- 468 * receive routine will process it.
- 469 */
- 470 eth_rx();
- 471
- 472 /*
- 473 * Abort if ctrl-c was pressed.
- 474 */
- 475 if (ctrlc()) {
- 476 /* cancel any ARP that may not have completed */
- 477 NetArpWaitPacketIP = 0;
- 478
- 479 net_cleanup_loop();
- 480 eth_halt();
- 481 /* Invalidate the last protocol */
- 482 eth_set_last_protocol(BOOTP);
- 483
- 484 puts( "\nAbort\n" );
- 485 /* include a debug print as well as incase the debug
- 486 messages are directed to stderr */
- 487 debug_cond(DEBUG_INT_STATE, "--- NetLoop Abort!\n" );
- 488 goto done;
- 489 }
- …………
- 522 switch (net_state) {
- 523
- 524 case NETLOOP_RESTART:
- 525 NetRestarted = 1;
- 526 goto restart;
- 527
- 528 case NETLOOP_SUCCESS:
- 529 net_cleanup_loop();
- 530 if (NetBootFileXferSize > 0) {
- 531 char buf[20];
- 532 printf( "Bytes transferred = %ld (%lx hex)\n" ,
- 533 NetBootFileXferSize,
- 534 NetBootFileXferSize);
- 535 sprintf(buf, "%lX" , NetBootFileXferSize);
- 536 setenv( "filesize" , buf);
- 537
- 538 sprintf(buf, "%lX" , (unsigned long)load_addr);
- 539 setenv( "fileaddr" , buf);
- 540 }
- 541 if (protocol != NETCONS)
- 542 eth_halt();
- 543 else
- 544 eth_halt_state_only();
- 545
- 546 eth_set_last_protocol(protocol);
- 547
- 548 ret = NetBootFileXferSize;
- 549 debug_cond(DEBUG_INT_STATE, "--- NetLoop Success!\n" );
- 550 goto done;
- 551
- 552 case NETLOOP_FAIL:
- 553 net_cleanup_loop();
- 554 /* Invalidate the last protocol */
- 555 eth_set_last_protocol(BOOTP);
- 556 debug_cond(DEBUG_INT_STATE, "--- NetLoop Fail!\n" );
- 557 goto done;
- 558
- 559 case NETLOOP_CONTINUE:
- 560 continue ;
- 561 }
- 562 }
- 563
- 564 done:
- 565 #ifdef CONFIG_CMD_TFTPPUT
- 566 /* Clear out the handlers */
- 567 net_set_udp_handler( NULL );
- 568 net_set_icmp_handler( NULL );
- 569 #endif
- 570 return ret;
- 571 }
The function parameter is DNS. Line 352 initializes network information, reads the values of environment variables such as ipaddr, gatewayip, netmask, serverip, dnsip, etc. and copies them to the corresponding global variables. - static void NetInitLoop(void)
- {
- static int env_changed_id;
- int env_id = get_env_id();
-
- /* update only when the environment has changed */
- if (env_changed_id != env_id) {
- NetOurIP = getenv_IPaddr( "ipaddr" );
- NetOurGatewayIP = getenv_IPaddr( "gatewayip" );
- NetOurSubnetMask = getenv_IPaddr( "netmask" );
- NetServerIP = getenv_IPaddr( "serverip" );
- NetOurNativeVLAN = getenv_VLAN( "nvlan" );
- NetOurVLAN = getenv_VLAN( "vlan" );
- #if defined(CONFIG_CMD_DNS)
- NetOurDNSIP = getenv_IPaddr( "dnsip" );
- #endif
- env_changed_id = env_id;
- }
- memcpy(NetOurEther, eth_get_dev()->enetaddr, 6);
-
- return ;
- }
Line 367 performs a switch operation on the incoming parameters, and different protocols enter different processing flows. Line 428 executes DnsStart(). - 197 void
- 198 DnsStart(void)
- 199 {
- 200 debug( "%s\n" , __func__);
- 201
- 202 NetSetTimeout(DNS_TIMEOUT, DnsTimeout);
- 203 net_set_udp_handler(DnsHandler);
- 204
- 205 DnsSend();
- 206 }
The function net_set_udp_handler() on line 203 mainly registers the callback function DnsHandler() of the DNS protocol to the callback pointer udp_packet_handler of the UDP protocol. - void net_set_udp_handler(rxhand_f *f)
- {
- debug_cond(DEBUG_INT_STATE, "--- NetLoop UDP handler set (%p)\n" , f);
- if (f == NULL )
- udp_packet_handler = dummy_handler; //Register to udp protocol callback function pointer
- else
- udp_packet_handler = f;
- }
DnsStart() will eventually call the function DnsSend() to send the DNS protocol data packet, which fills the UDP data packet according to the DNS protocol. - 37 static void
- 38 DnsSend(void)
- 39 {
- 40 struct header *header;
- 41 int n, name_len;
- 42 uchar *p, *pkt;
- 43 const char *s;
- 44 const char * name ;
- 45 enum dns_query_type qtype = DNS_A_RECORD;
- 46
- 47 name = NetDNSResolve;
- 48 pkt = p = (uchar *)(NetTxPacket + NetEthHdrSize() + IP_UDP_HDR_SIZE);
- 49
- 50 /* Prepare DNS packet header */
- 51 header = (struct header *) pkt;
- 52 header->tid = 1;
- 53 header->flags = htons(0x100); /* standard query */
- 54 header->nqueries = htons(1); /* Just one query */
- 55 header->nanswers = 0;
- 56 header->nauth = 0;
- 57 header->nother = 0;
- 58
- 59 /* Encode DNS name */
- 60 name_len = strlen( name );
- 61 p = (uchar *) &header->data; /* For encoding host name into packet */
- 62
- 63 do {
- 64 s = strchr( name , '.' );
- 65 if (!s)
- 66 s = name + name_len;
- 67
- 68 n = s - name ; /* Chunk length */
- 69 *p++ = n; /* Copy length */
- 70 memcpy(p, name , n); /* Copy chunk */
- 71 p += n;
- 72
- 73 if (*s == '.' )
- 74 n++;
- 75
- 76 name += n;
- 77 name_len -= n;
- 78 } while (*s != '\0' );
- 79
- 80 *p++ = 0; /* Mark end of host name */
- 81 *p++ = 0; /* Some servers require double null */
- 82 *p++ = (unsigned char ) qtype; /* Query Type */
- 83
- 84 *p++ = 0;
- 85 *p++ = 1; /* Class: inet, 0x0001 */
- 86
- 87 n = p - pkt; /* Total packet length */
- 88 debug( "Packet size %d\n" , n);
- 89
- 90 DnsOurPort = random_port();
- 91
- 92 NetSendUDPPacket(NetServerEther, NetOurDNSIP, DNS_SERVICE_PORT,
- 93 DnsOurPort, n);
- 94 debug( "DNS packet sent\n" );
- 95 }
Lines 51-57 fill the DNS protocol header according to the DNS protocol. The first address of the data frame is NetTxPacket. Here, the pointers pkt and p are used to fill the DNS data frame. Lines 60-85 fill the host name to be parsed into the data packet according to the protocol format requirements. Line 87 calculates the length of the data packet. Line 90 generates a random port number. Lines 92-93 call the UDP protocol sending function NetSendUDPPacket(). The parameters are: Ethernet header information, DNS server IP address, DNS server port number, our DNS service port number, and data packet length. - 688 int NetSendUDPPacket(uchar *ether, IPaddr_t dest, int dport, int sport,
- 689 int payload_len)
- 690 {
- 691 uchar *pkt;
- 692 int eth_hdr_size;
- 693 int pkt_hdr_size;
- 694
- 695 /* make sure the NetTxPacket is initialized (NetInit() was called) */
- 696 assert(NetTxPacket != NULL );
- 697 if (NetTxPacket == NULL )
- 698 return -1;
- 699
- 700 /* convert to new style broadcast */
- 701 if (dest == 0)
- 702 dest = 0xFFFFFFFF;
- 703
- 704 /* if broadcast, make the ether address a broadcast and don't do ARP */
- 705 if (dest == 0xFFFFFFFF)
- 706 ether = NetBcastAddr;
- 707
- 708 pkt = (uchar *)NetTxPacket;
- 709
- 710 eth_hdr_size = NetSetEther(pkt, ether, PROT_IP);
- 711 pkt += eth_hdr_size;
- 712 net_set_udp_header(pkt, dest, dport, sport, payload_len);
- 713 pkt_hdr_size = eth_hdr_size + IP_UDP_HDR_SIZE;
- 714
- 715 /* if MAC address was not discovered yet, do an ARP request */
- 716 if (memcmp(ether, NetEtherNullAddr, 6) == 0) {
- 717 debug_cond(DEBUG_DEV_PKT, "sending ARP for %pI4\n" , &dest);
- 718
- 719 /* save the ip and eth addr for the packet to send after arp */
- 720 NetArpWaitPacketIP = dest;
- 721 NetArpWaitPacketMAC = ether;
- 722
- 723 /* size of the waiting packet */
- 724 NetArpWaitTxPacketSize = pkt_hdr_size + payload_len;
- 725
- 726 /* and do the ARP request */
- 727 NetArpWaitTry = 1;
- 728 NetArpWaitTimerStart = get_timer(0);
- 729 ArpRequest();
- 730 return 1; /* waiting */
- 731 } else {
- 732 debug_cond(DEBUG_DEV_PKT, "sending UDP to %pI4/%pM\n" ,
- 733 &dest, ether);
- 734 NetSendPacket(NetTxPacket, pkt_hdr_size + payload_len);
- 735 return 0; /* transmitted */
- 736 }
- 737 }
Lines 696-706 check parameters Line 710 sets the Ethernet header Line 713 sets the UDP protocol header Lines 716-730 If there is no destination MAC address, an ARP request must be sent first Line 734 calls the function NetSendPacket(), the parameters are: the first address of the data frame to be sent, the length of the data packet - 529 /* Transmit a packet */
- 530 static inline void NetSendPacket(uchar *pkt, int len)
- 531 {
- 532 (void) eth_send(pkt, len);
- 533 }
Line 532 calls the function dm9000_send() that we registered. This function has been analyzed. According to the flowchart, we return to the function NetLoop(). Lines 461-562 loop to receive network packets. Line 470 calls the network card driver receiving function eth_rx() - int eth_rx(void)
- {
- if (!eth_current)
- return -1;
-
- return eth_current->recv(eth_current);
- }
The eth_current->recv(eth_current) function is the receiving function dm9000_rx() of the network card we registered. We have analyzed this function in the previous chapter. Finally, the data frame is uploaded to the protocol stack by calling the function NetReceive(). - 943 void
- 944 NetReceive(uchar *inpkt, int len)
- 945 {
- 946 struct ethernet_hdr *et;
- 947 struct ip_udp_hdr *ip;
- 948 IPaddr_t dst_ip;
- 949 IPaddr_t src_ip;
- 950 int eth_proto;
- …
- 957
- 958 NetRxPacket = inpkt;
- 959 NetRxPacketLen = len;
- 960 et = (struct ethernet_hdr *)inpkt;
- 961
- 962 /* too small packet? */
- 963 if (len < ETHER_HDR_SIZE)
- 964 return ;
- 965
- …
- 984
- 985 eth_proto = ntohs(et->et_protlen);
- 986
- 987 if (eth_proto < 1514) {
- 988 struct e802_hdr *et802 = (struct e802_hdr *)et;
- …
- 997
- 998 } else if (eth_proto != PROT_VLAN) { /* normal packet */
- 999 ip = (struct ip_udp_hdr *)(inpkt + ETHER_HDR_SIZE);
- 1000 len -= ETHER_HDR_SIZE;
- 1001
- 1002 } else { /* VLAN packet */
- …
- 1026 }
- 1027
- …
- 1045 switch (eth_proto) {
- …
- 1056 case PROT_IP:
- 1057 debug_cond(DEBUG_NET_PKT, "Got IP\n" );
- 1058 /* Before we start poking the header, make sure it is there */
- 1059 if (len < IP_UDP_HDR_SIZE) {
- 1060 debug( "len bad %d < %lu\n" , len,
- 1061 (ulong)IP_UDP_HDR_SIZE);
- 1062 return ;
- 1063 }
- 1064 /* Check the packet length */
- 1065 if (len < ntohs(ip->ip_len)) {
- 1066 debug( "len bad %d < %d\n" , len, ntohs(ip->ip_len));
- 1067 return ;
- 1068 }
- 1069 len = ntohs(ip->ip_len);
- 1070 debug_cond(DEBUG_NET_PKT, "len=%d, v=%02x\n" ,
- 1071 len, ip->ip_hl_v & 0xff);
- 1072
- 1073 /* Can't deal with anything except IPv4 */
- 1074 if ((ip->ip_hl_v & 0xf0) != 0x40)
- 1075 return ;
- 1076 /* Can't deal with IP options (headers != 20 bytes) */
- 1077 if ((ip->ip_hl_v & 0x0f) > 0x05)
- 1078 return ;
- 1079 /* Check the Checksum of the header */
- 1080 if (!NetCksumOk((uchar *)ip, IP_HDR_SIZE / 2)) {
- 1081 debug( "checksum bad\n" );
- 1082 return ;
- 1083 }
- 1084 /* If it is not for us, ignore it */
- 1085 dst_ip = NetReadIP(&ip->ip_dst);
-
- 1092 /* Read source IP address for later use */
- 1093 src_ip = NetReadIP(&ip->ip_src);
-
-
- 1184 /*
- 1185 * IP header OK. Pass the packet to the current handler.
- 1186 */
- 1187 (*udp_packet_handler)((uchar *)ip + IP_UDP_HDR_SIZE,
- 1188ntohs(ip->udp_dst),
- 1189 src_ip,
- 1190ntohs(ip->udp_src),
- 1191 ntohs(ip->udp_len) - UDP_HDR_SIZE);
- 1192 break;
- 1193 }
- 1194 }
Parameter inpkt: points to the received Ethernet packet header len: the length of the received packet Line 960 Variable NetRxPacket points to the received data header, the Ethernet packet header locates the Ethernet protocol header Line 985 Extract the protocol field from the Ethernet protocol header, which indicates whether the following is the IP protocol Line 999 Parse the IP protocol header Line 1045 Perform switch operation according to the Ethernet header protocol Lines 1059~1083 Check the legitimacy of the protocol header Line 1085 Read the destination IP address Line 1093 Read the source IP address, Line 1187 IP protocol header parsed successfully, call the udp protocol callback function udp_packet_handler(), which registered DnsHandler in the previous DnStart() - 104 static void
- 105 DnsHandler(uchar *pkt, unsigned dest, IPaddr_t sip, unsigned src, unsigned len)
- 106 {
- 193
- 194 net_set_state(NETLOOP_SUCCESS);
- 195 }
This function is used to parse the DNS protocol. We will not explain it in detail here. After the successful parsing, line 194 sets the current execution state to NETLOOP_SUCCESS. The code returns to the function NetLoop(). Lines 470 and 475 determine whether the ctrl+c shortcut key is pressed and perform operations. Lines 522 to 562 process the execution results and include them in the statistical information. Line 564 If net_state is NETLOOP_SUCCESS or NETLOOP_FAIL, it will eventually enter done, thereby emptying the udp callback function. If net_state is NETLOOP_CONTINUE, it indicates that there are still subsequent data packets to be received, then it returns to line 461 and continues to receive the next data packet. At this point, the analysis of the DNS protocol processing flow is completed. You can analyze the processing flows of several other protocols based on this flow. Common problems Sometimes the DM9000A ID can be read. Continuous operation can read the DM9000A ID, but after a while the operation cannot read the DM9000A ID. Through debugging, add a delay operation in the dm9000_reset function, and the DM9000A ID can be read normally. - 277 do {
- 278 DM9000_DBG( "resetting the DM9000, 2nd reset\n" );
- 279 udelay(25); /* Wait at least 20 us */
- 280 } while (DM9000_ior(DM9000_NCR) & 1);
- 281 udelay(150);
- 282 /* Check whether the ethernet controller is present */
- 283 if ((DM9000_ior(DM9000_PIDL) != 0x0) ||
- 284 (DM9000_ior(DM9000_PIDH) != 0x90))
- 285 printf( "ERROR: resetting DM9000 -> not responding\n" );
|